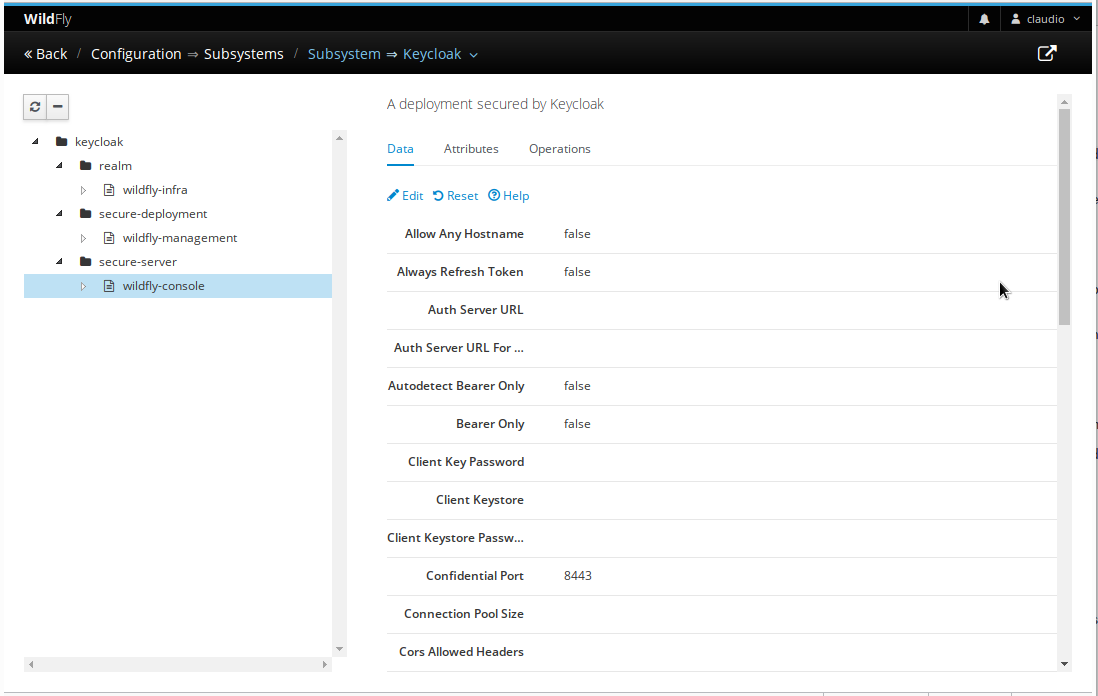
Keycloak SSO
When user configures Wildfly to authenticate user to Keycloak SSO, HAL supports the authentication the following way:
- HAL redirects the login attempt to keycloak server, if successful redirect back to HAL.
- Provide the logout option in HAL to call the logout page on keycloak. This is displayed under the username in the header section.
- Displays basic Keycloak settings in the Access Control page.
- Displays a link to user profile on Keycloak server.
- Point the Access Control link in the Homepage to the Keycloak server URL.
The Wildfly Access Control mechanism to manage users and roles should be disabled, because they are managed in Keycloak server. However RBAC continues to works in Wildfly to fine tune permission settings.
How to setup Wildfly to use Keycloak authentication
Warning
- The authentication only works in standalone mode, as the wildfly keycloak adapter doesn’t support domain mode yet.
Login attempt
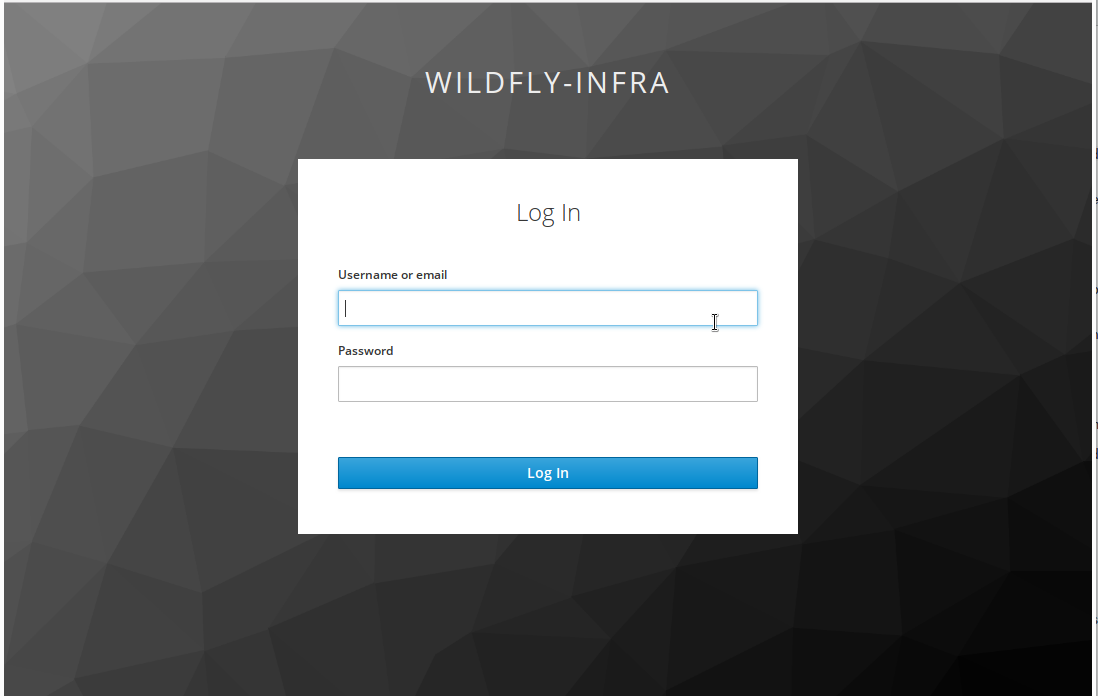
When user wants to access HAL management console, it redirects to Keycloak server and presents the authentication form.
Access control
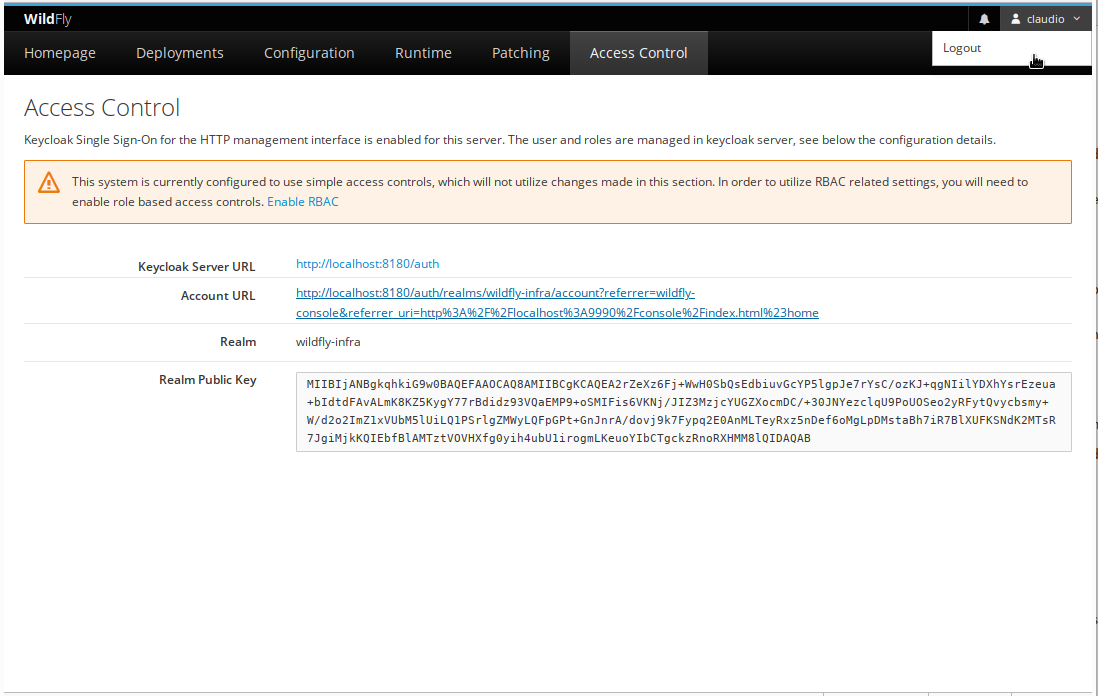
The Access Control top level menu, shows basic Keycloak settings:
- User information
- Keycloak server url
- Keycloak account profile
- Realm name
- Realm public key
If RBAC is not set, there is a warning at the top warning the user, there is no role based access control mechanism, and there is an option to enable it.
Also, there is the “Logout” option in the header section.
Account Profile
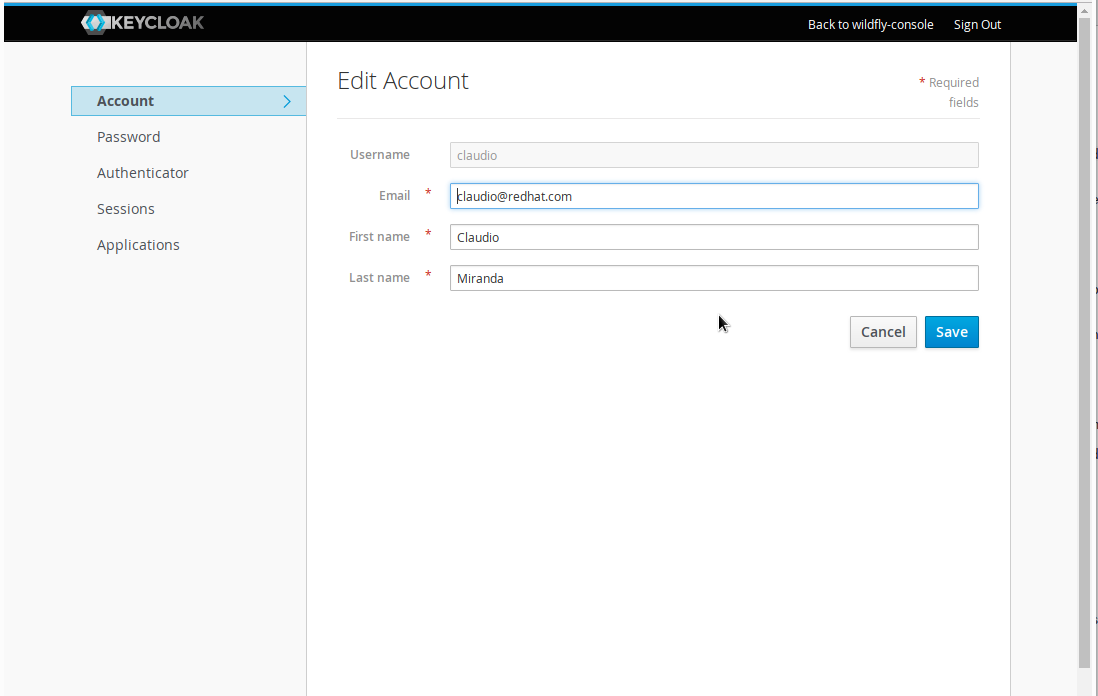
When user wants to view and edit basic user information on keycloak server, there is a link in the Access Control page, that redirects to Keycloak server. The page enables users to:
- Edit name and email.
- Change password.
- List all login sessions.
- Logout from all sessions.
- List keycloak application the user is entitled to log in.